Time
2022
Project Type
Thesis project
Skills&Tools
Figma, Adobe PS
Blender, Unity
Bet on virtual
From novelists, social networking (ex. Facebook), VR companies, NFT platforms (ex. Crypto.com) to game developers (ex. Roblox), everyone is talking about the metaverse.
Why do people bet on virtual and keep investing the metaverse concept? I think the real fascination of the metaverse is our ownership of virtual assets. It is claimed that these digital assets are not controlled by centralized corporations, that data is authenticated and cannot be manipulated at will, and that purchased credentials are broadcast to the public and cannot be wiped. So, your digital assets are like real assets, they are yours and they are stable. They have long-lasting value.

A reflection on humans in digital life, digital products, digital assets, etc
The project uses design as an practice strategy to reflect on the metaverse and NFT assets these days. It is a visual design practice to investigate the inner attributions of the digital products. I use a series of 'hack' programs built in Unity to demonstrate the instability under various scenarios. It visualizes what will affect our digital assets and how will they affect? Also, what will it look like when these assets are unstable.

Instable Assets
A digital asset may be a model, a photograph, a piece of music or even a twitter. As long as a virtual object has a unique digital signature, it can be considered as a digital asset. I create many 3D models that we can own in the future to better demonstrate the instability














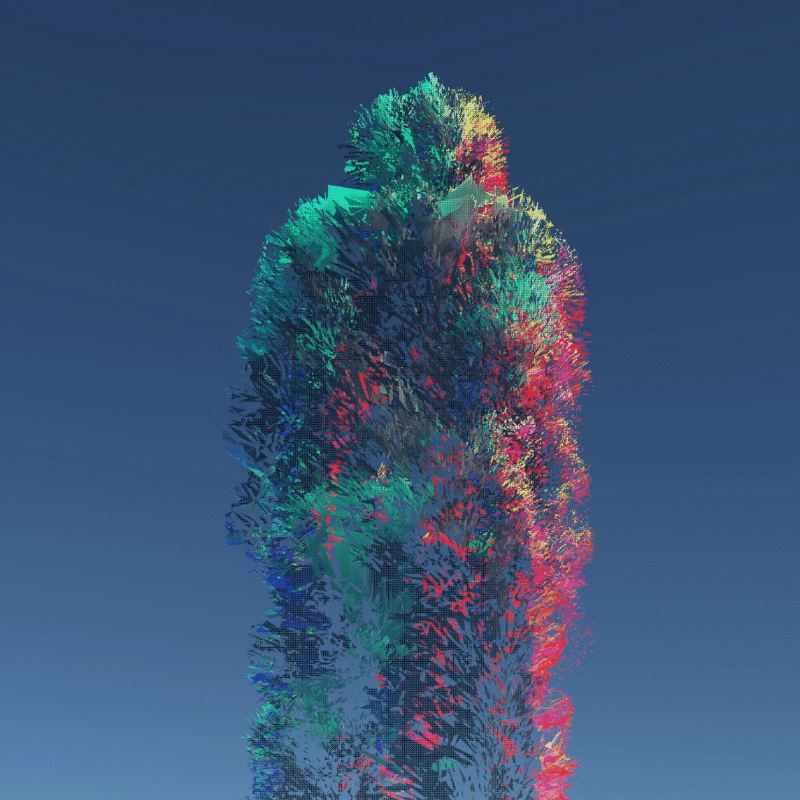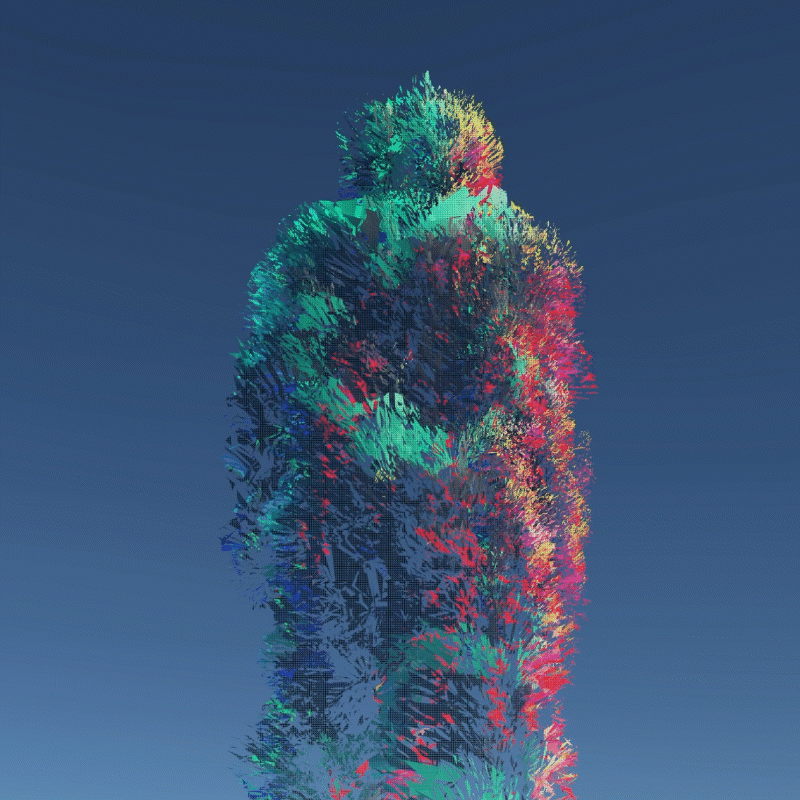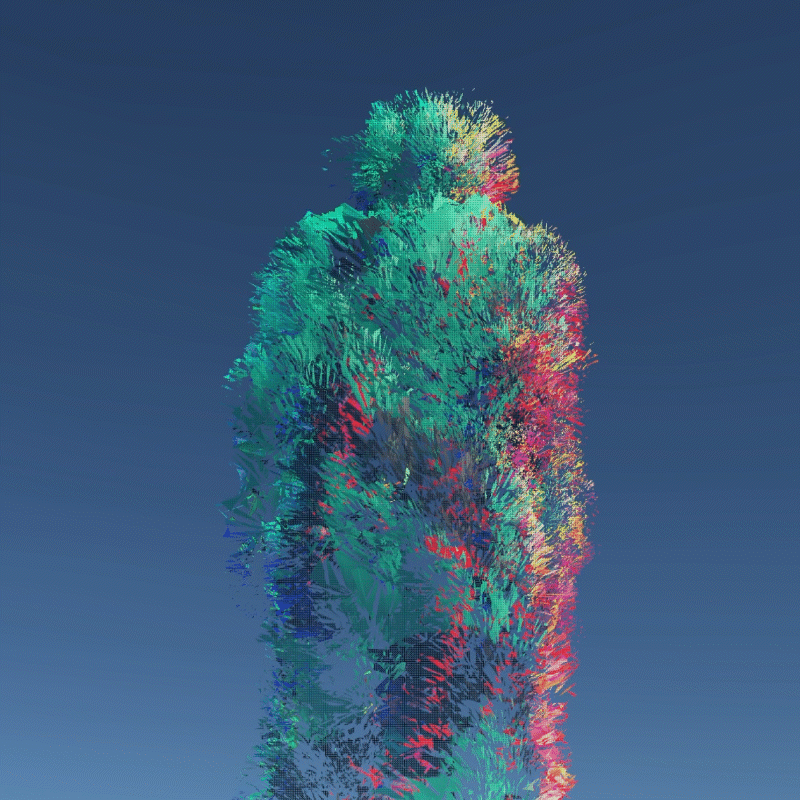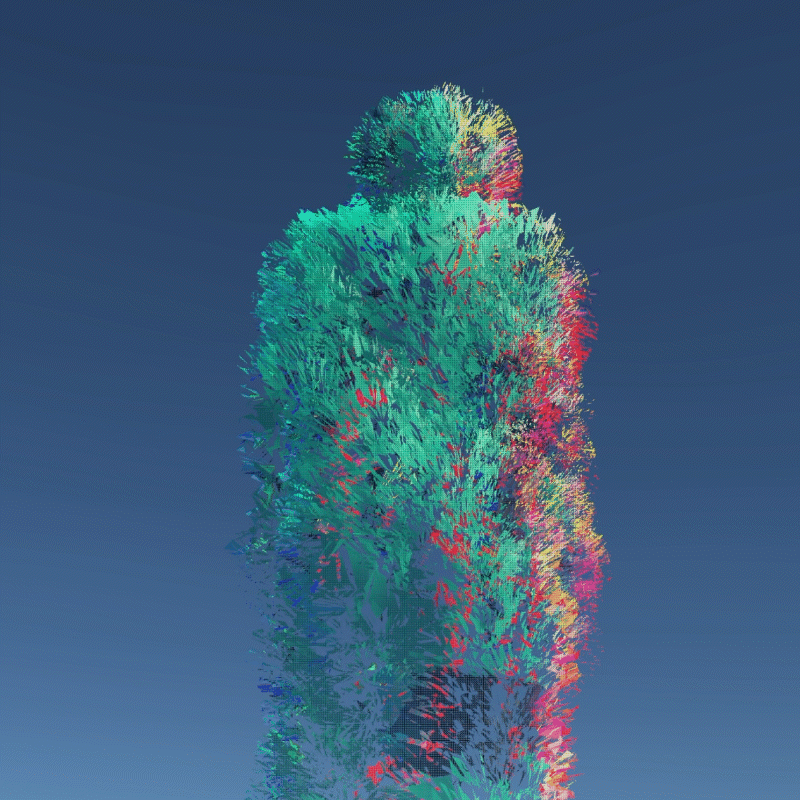
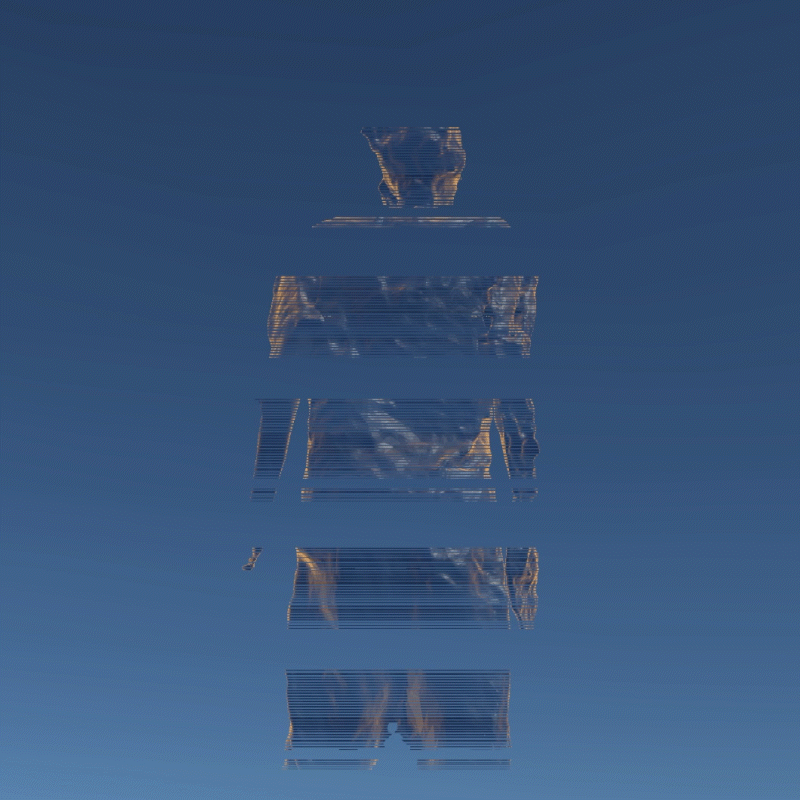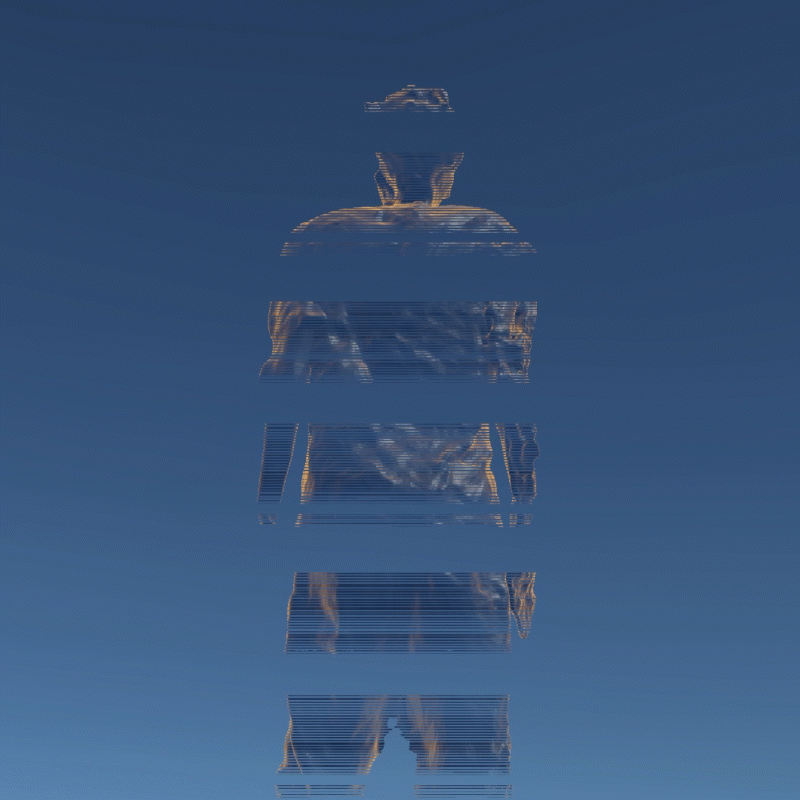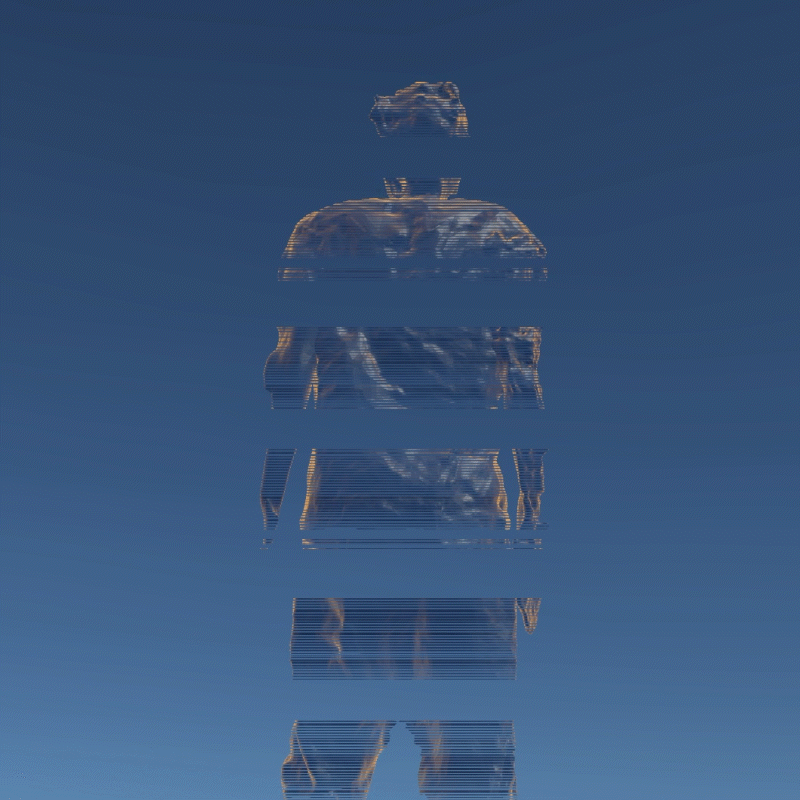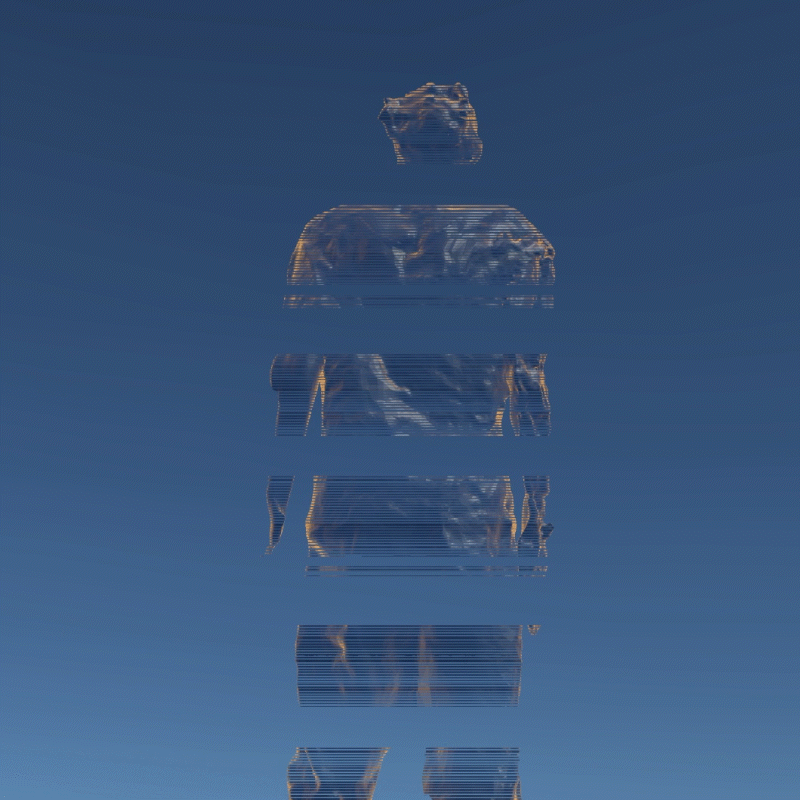


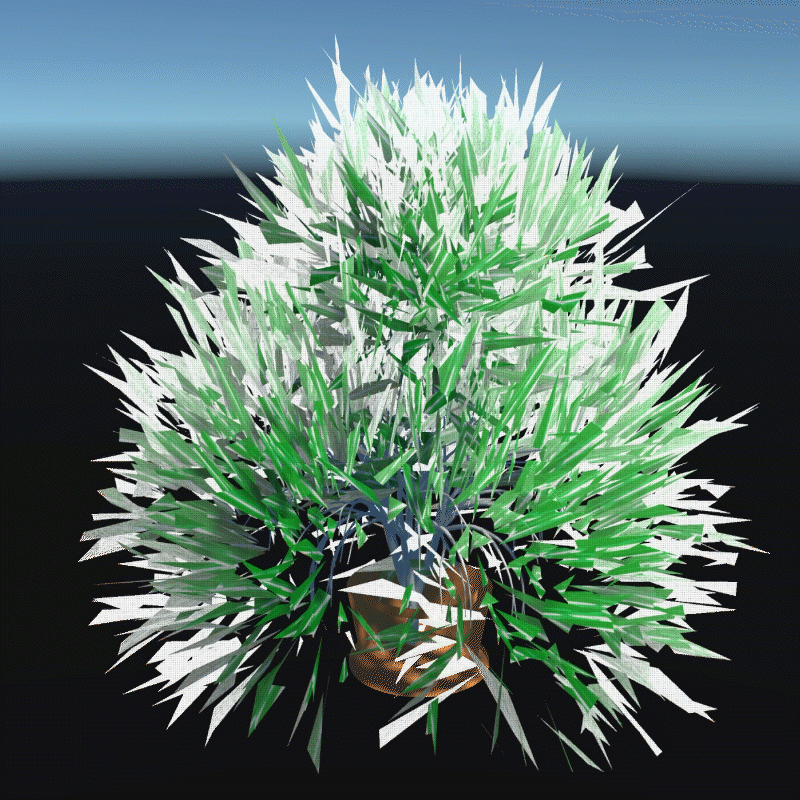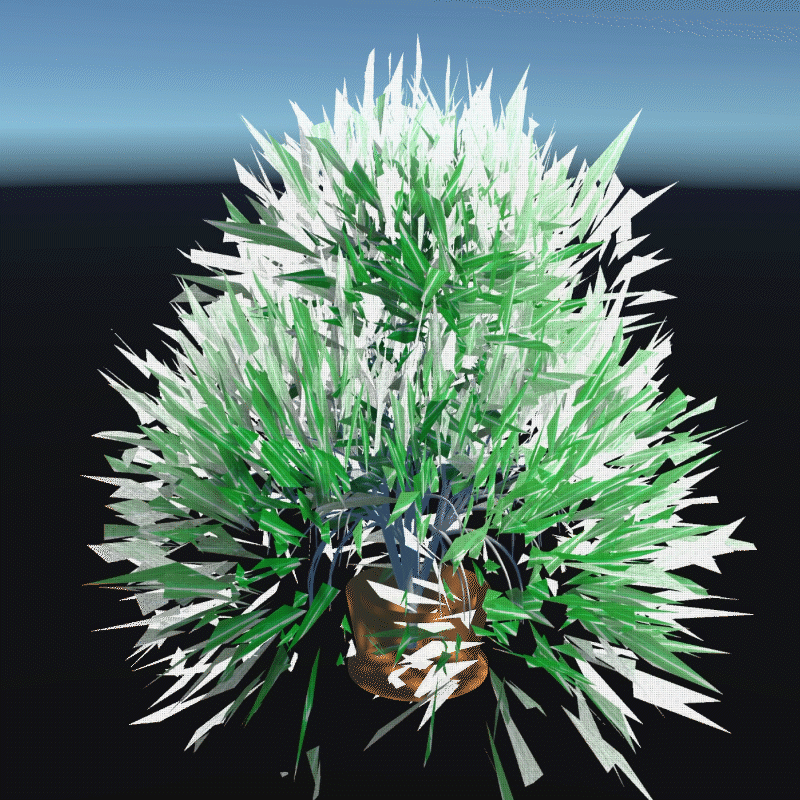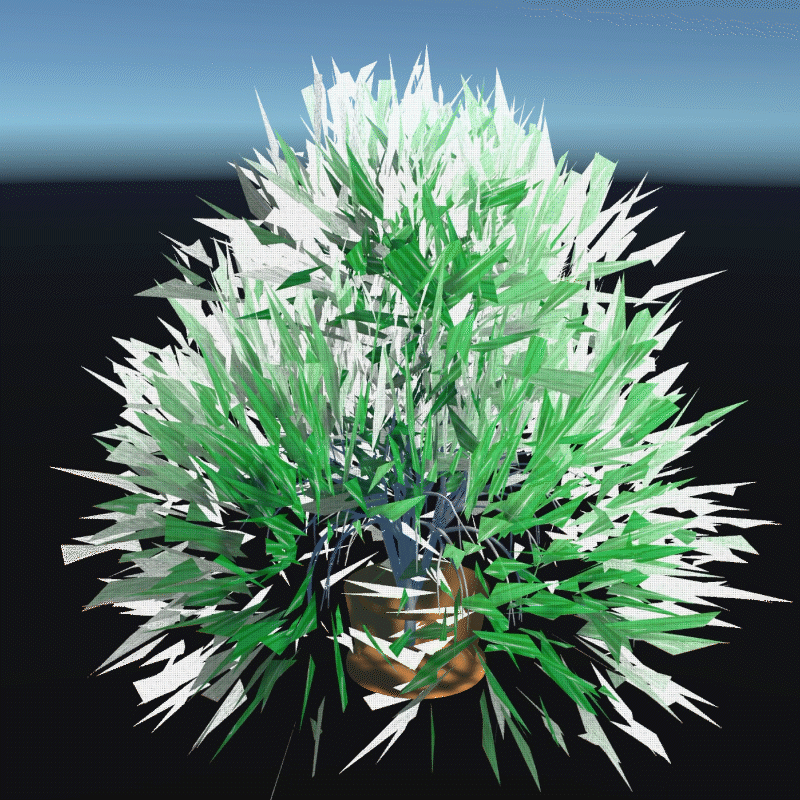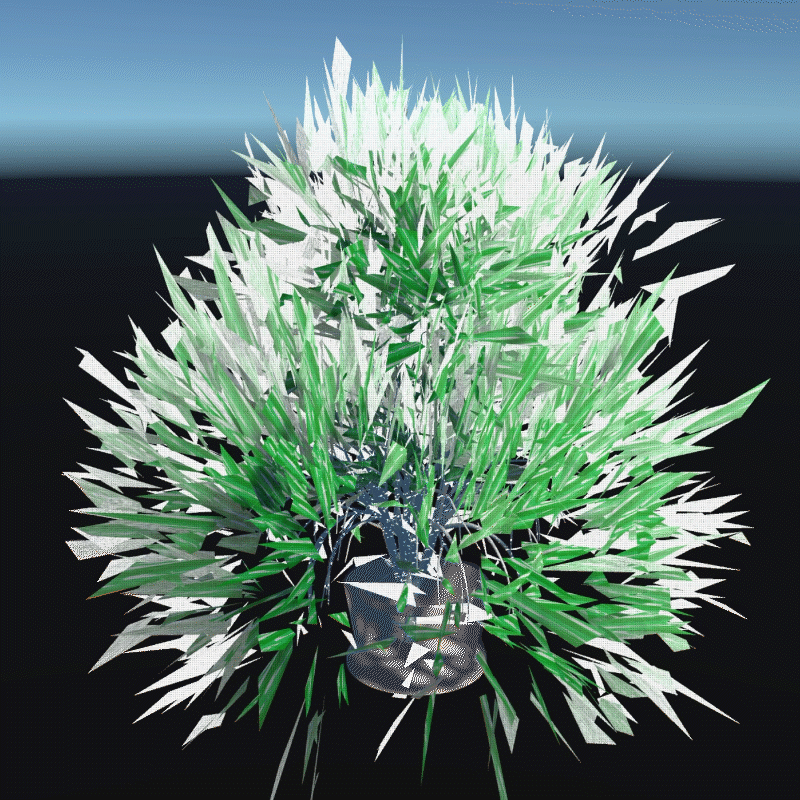

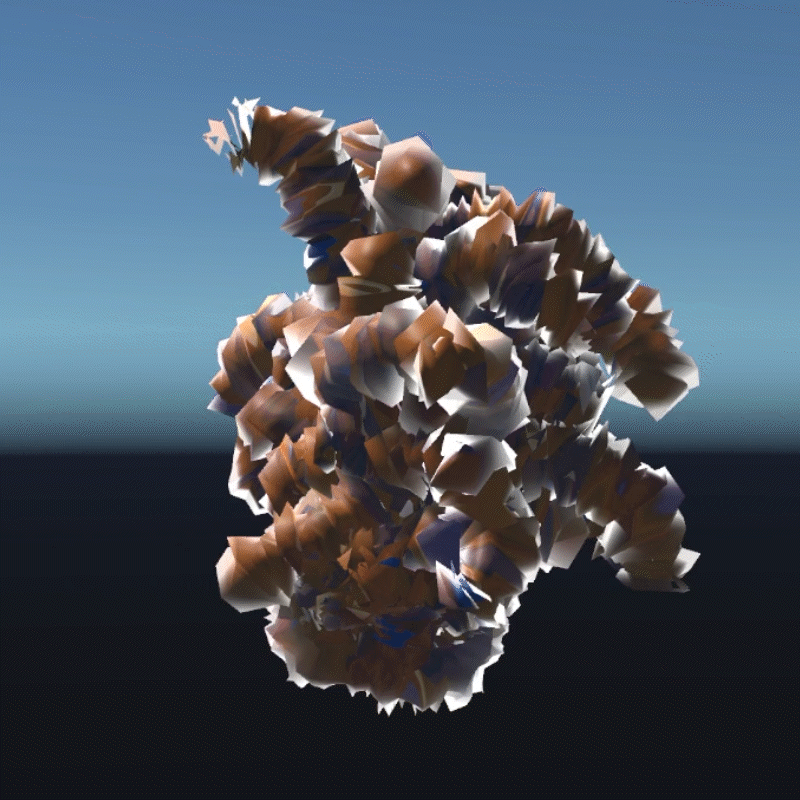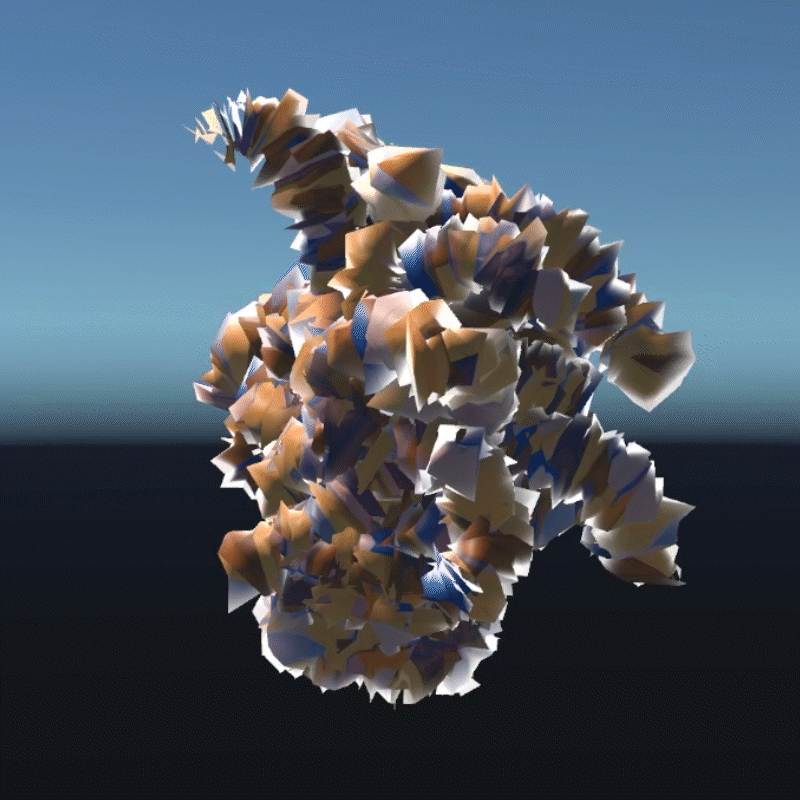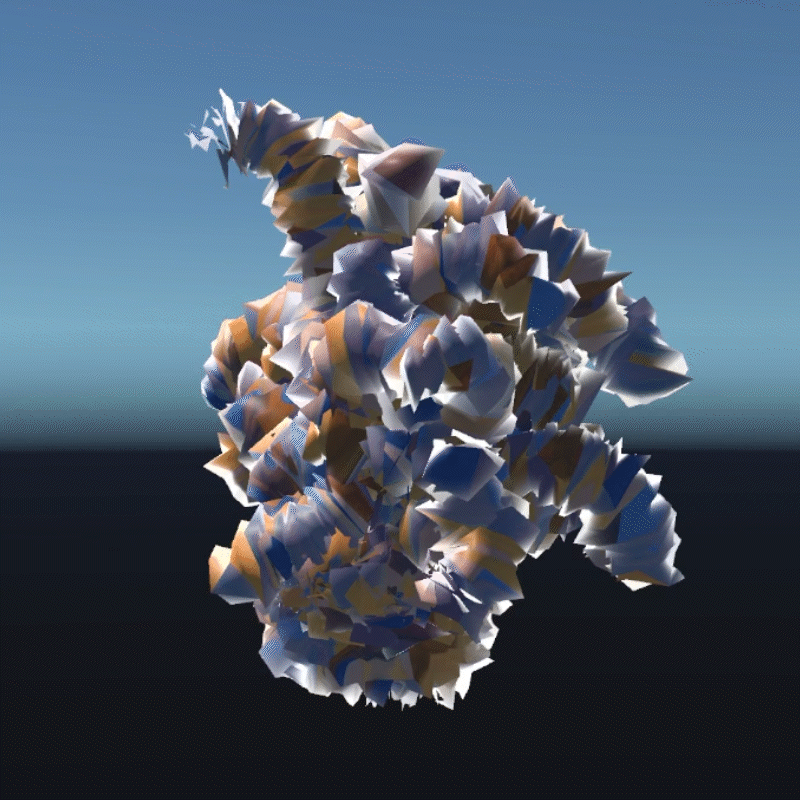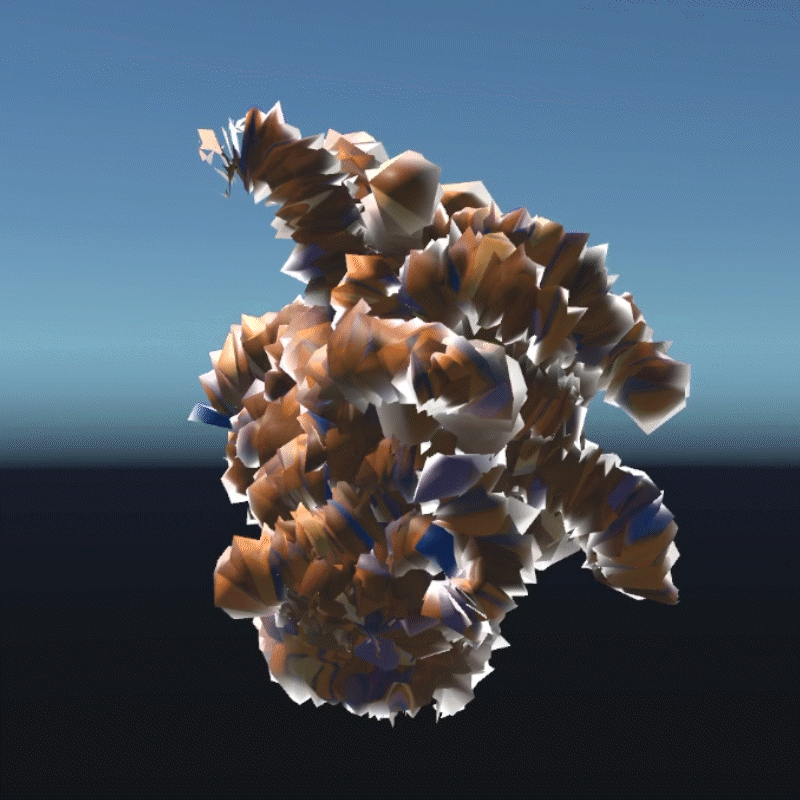


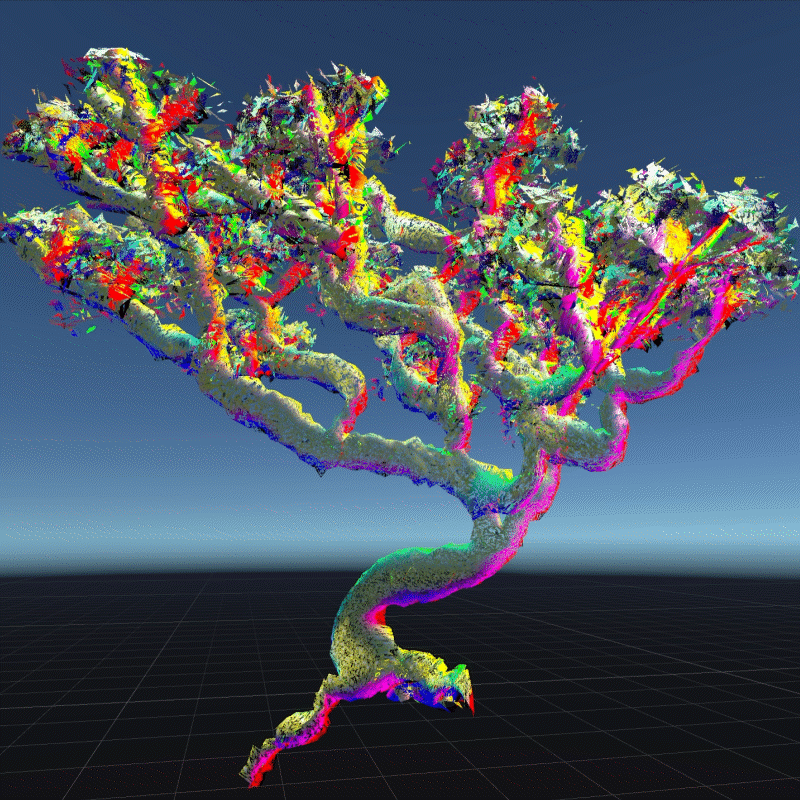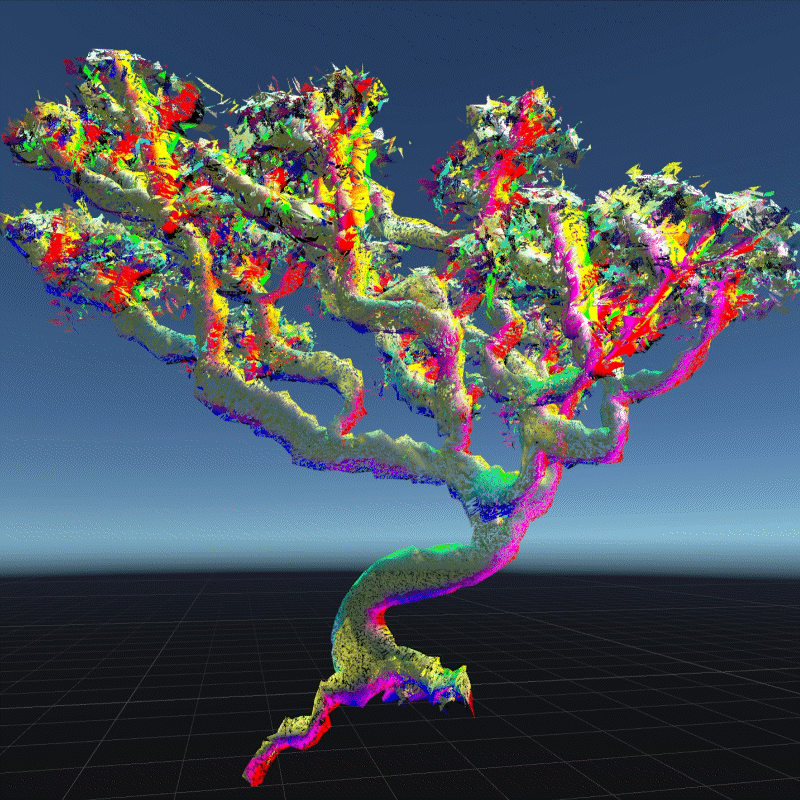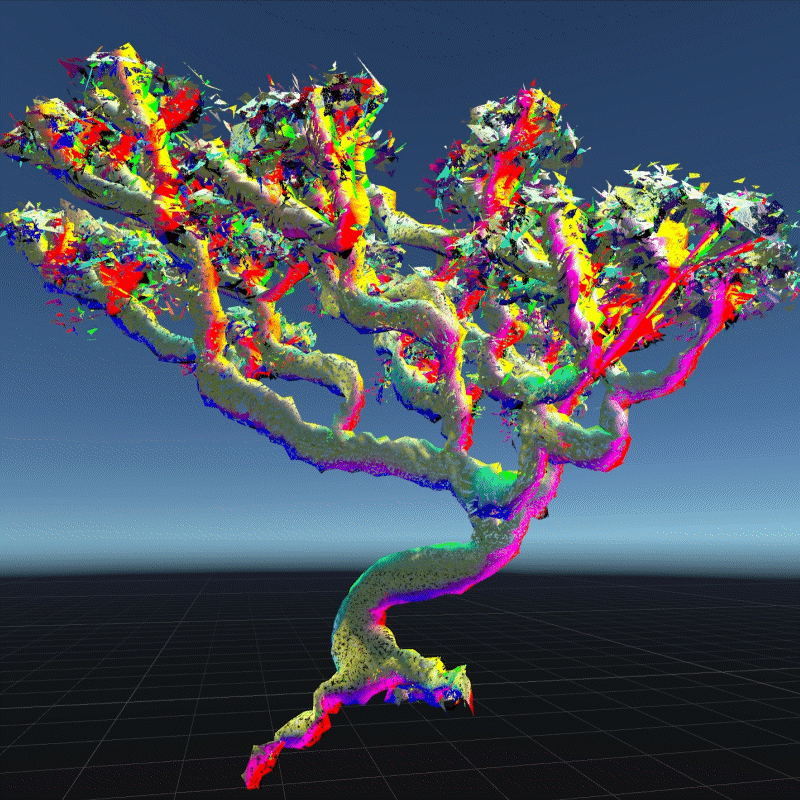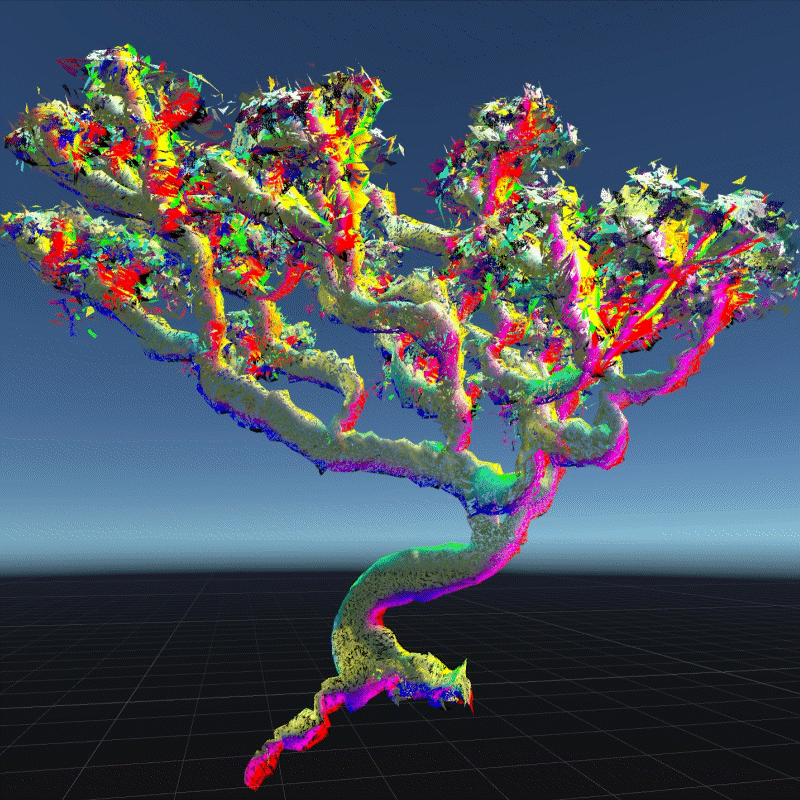






My design expressed three aspects of their instability. Including, Changing Environment, Virus and Bugs, Hacker Actions. It is also a provocation to think about the value of digital assets obtained in the metaverse.
Hack_01-03.exe (Changing Environment)
The coding environment is not our physical world. They are changing rapidly. The video and image formats of two decades ago may not be readable now. If we have digital assets that appear completely different, or even unreadable in different environments. These assets are instable and becomes meaningless.
In this program, you can see that I have placed many purchased assets in a virtual space. Trees, plants, mountain, and even my own avatar. These three trees around are indicators of different environments. When approaching different trees, the whole system environment changes. Depending on the environment, the virtual assets change shape from physical analog to digital styles, or to pixel squares. This hack program shows the instability of virtual assets in different environments, and their possible patterns.



Hack_04.exe (Virus invasion)
Virus is an external program that can infect and corrupt our digital assets. These assets can become unreadable or unrecognizable. In this program, I simulated how the digital assets would look like if they were invaded by a virus. I used a pattern similar to the inside of a transistor as the background of the environment. You can see that most of the digital assets have been turned into various pieces and are flashing continuously. Without the hints in the previous program, most people probably wouldn't be able to recognize what these things are. This demonstrates that a virus is destroying virtual assets. You can walk around trying to clear the virus, but of course it doesn't always work, and even your avatar may be infected. This virtual office-like area is where the infection is most severe. Here is a hint that when we are connected to the Internet, our digital assets are at risk from the virus.

Hack_05.exe (Inside Bugs)
Bugs are flaws within a program, and bugs are always present, regardless of the digital system. It is a potential hazard that can lead to serious consequences if someone misuses it. In this program, I simulated what happens when a user triggers a bug. At first, the environment and virtual assets look normal. Notice that you have some plants, a mountain, some dead trees and a big digital tree. But then you enter a bug and fall inside the model. This allows you to replicate your digital tree. Virtual assets are mostly authenticated by transforming them into NFTs so that they get a unique signature. However, if a bug occurs, it is possible to replicate them. The situation is different, imagine if this was a virtual currency and you were able to copy it using a bug. The consequences would be severe.

Hack_06.exe (Hacker Stealing)
Hacker Actions: Blockchain technology has always been touted for the security of digital assets, which are decentralized and untraceable. However, any system has vulnerabilities and hacking is still a risk that digital assets need to face.

Process&Iteration
For my thesis, at the very beginning, I knew I wanted to do something about digital art, react and think about digital transformation, digital assets. But I'm not so sure about how to express it. I have tried various things. First of all, I like to try to choose our digital twin, which is the avatar, to create. In the future, in the metaverse environment, our avatars will replace us, become the entrance to the metaverse, and become the interface for interaction and social interaction.


I try to explore the changes in digital avatars, from 2D images to animations. Then to the projection of personal image. I try to copy, scale, arrange, put into a virtual space. I also tried placing the avatar in the AR scene.


I chose the Metaverse Portal and used Unity to make a concept that expresses the Metaverse Square. Avatars can constantly change in this space to adapt to a dynamic, changing, and real-time updated digital world.

As the iteration progressed, I found that keeping the avatar element had so many possibilities that it was difficult for me to design it in a specific space or area. I think I've lost control over the shape of the avatar, or the possibility of explicitly conveying avatars through sets of animations, programs, or AR/VR experiences. I wanted to express digital art, and I ended up jumping out of avatars and opting for the concept of digital assets to include avatars. Their variations, their free forms, ultimately point to one word, instability.

I chose to present this instability, which is visually represented as various forms of digital assets. The 3D model assets can be completely different from physical shape to shining fragments, from workable materials to unrecognizable broken pieces, from high dimensional shaders to low-poly cubes. There is no way to guarantee their stability. And they can be switched with each other easily. I believe it is the most fascinating feature of digital assets in the future.






